Sign Up to our social questions and Answers Engine to ask questions, answer people’s questions, and connect with other people.
Lost your password? Please enter your email address. You will receive a link and will create a new password via email.
Please briefly explain why you feel this question should be reported.
Please briefly explain why you feel this answer should be reported.
Please briefly explain why you feel this user should be reported.
Which Statement Regarding The Selection Of A Hard Drive Is Accurate?
Which Statement Regarding The Selection Of A Hard Drive Is Accurate? The magnetic drives will have a larger capacity when compared with solid-state drives. Today, let us discuss magnetic drives and the difference between magnetic and solid-state drives. The magnetic drive which usually called the haRead more
Which Statement Regarding The Selection Of A Hard Drive Is Accurate?
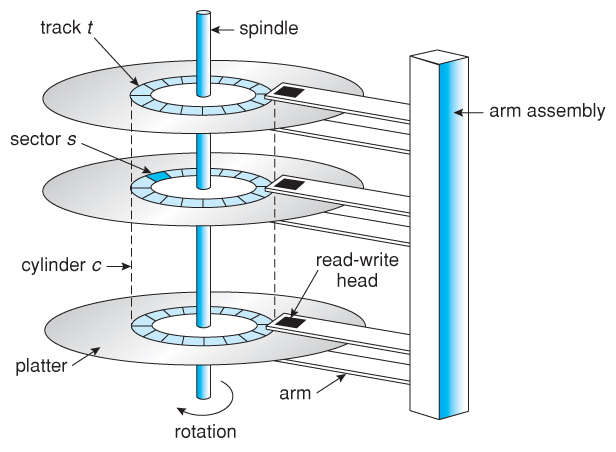
The magnetic drives will have a larger capacity when compared with solid-state drives. Today, let us discuss magnetic drives and the difference between magnetic and solid-state drives. The magnetic drive which usually called the hard disk or a hard drive. The floppy disks are also called magnetic disks. Let us know how a magnetic drive looks like, it has a spindle to which we can attach the platters. All the platters are attached to the spindle and rotate at the same speed. The below figure represents the structure of how the magnetic drive looks like.
The single platter has a surface that is covered with magnetic material on one side and the other.
We normally have the three platters that actually have the six surfaces. The data bits can be present on all the surfaces. We can access this data by having a simple magnetic head that is attached to an arm and another one at the lower surface.
All of these heads are attached to a head assembly that can move all the heads in unison. All the heads will be in the same position as the different platters. We move all of these heads at the same time. Each head can able to access its own surface and all of this will be going with the same distance in the spindle. This is called the track. All of the tracks will be at the same distance from the spindle that forms a shape called the cylinder. The cylinder will simple consists of one track from each surface and the tracks in the cylinders are the one can be accessed by the different heads at the same time.
The data along the one track is divided into the form of different sectors, and each sector will be the smallest unit that we can actually read.
Now, let us know what actually the solid-state drives are, it is like a data storage drive that can store the information in the computer. The solid-state drive can use flash memory in order to store the data when the system gets turned off. The solid-state drive has the same process as the traditional hard drives in accessing the data. This solid-state drive has common interfaces which are compatible with hardware drives. This solid-state drive uses some of the interfaces like m.2 and the SATA. Solid-state drives are quite different from traditional and mechanical drives. We can access the data much quicker in the solid-state drives and has a lower latency in it.
These solid-state drives are mostly used in the IBM think pads, and in the SanDisk corporation. The speed and the performance of the solid-state drive are much more than the hard disk drive. The SSD’s have speeds in the range of microseconds and the usually read and write speed is in the range of 400 to 500 Mbps. We can also use it as the sequential read and write with the speed of gigabytes per second.
See lessAt What Point During The Motherboard Installation Should You Install The Motherboard Drivers?
At What Point During The Motherboard Installation Should You Install The Motherboard Drivers? During the motherboard Installation, after the system gets rebooted without any errors, the motherboard drivers must be installed. Today, let us learn how to install the drivers. The motherboard drivers musRead more
At What Point During The Motherboard Installation Should You Install The Motherboard Drivers?
During the motherboard Installation, after the system gets rebooted without any errors, the motherboard drivers must be installed. Today, let us learn how to install the drivers. The motherboard drivers must be installed at last after the system get rebooted. These drivers are installed in order to control the motherboard and its internal graphics.
Now, let us learn how to install the motherboard drivers that will make the windows run more efficiently, we will set up the internal graphics driver so that we can set the resolution for the motherboard and we can install the Microsoft windows, anti-virus programs, and so on.
Right-click on the desktop and go to the screen resolution and click on the screen resolution window that shows the size. We need to install the drivers that control the settings of the display, if the graphic card has to get installed in the computer, the PCI express the slot on the motherboard, then we will have a disc with the driver on it for your graphics card and the driver should also be installed. Put the disk that came into the motherboard into the DVD player and after 30 seconds the window start running. that shows the ISO assetup.exe file. If this autoplay window does not open just we need to go to the computer, the DVD player will show the assetup.exe, now, double click on it, it will show the process.
Motherboard drivers are the parts of the computers that can control all the functions. The motherboard drivers are like the software interface that is between the computer hardware and the motherboard in the system software. The motherboard controls the entire system which can fully function and can update all the drivers. The updated drivers are important for the computer functions to update the motherboard drivers.
All individuals must know the manufacturing and the model of the motherboard where originally motherboard was simple with some of the few extra features. All these motherboards have a handful of all the necessary pieces and ports where users can add whatever they want.
The new types of motherboards have the embedded sound and all the network systems and even have external hard drive hookups. These are more complicated at the hardware and the driver’s point.
The computer drivers are the software systems that can instruct all the computer components and the software. The proper use of the software is the basic understanding of all the hardware functions, the hardware functions include operating systems. The drivers provide some of the additional information on how to use the specific model of the hardware. The motherboard drivers often end up separated into the different installation packages that affect one aspect of the board, the basic driver for any of the motherboards. All these drivers cover the basic functionality of the board, it is the driver that sits right at the heart of the computer. Each additional sectional of the board would have its own separate drivers in it.
See lessWhich Statement Regarding The Usb Standard And Usb Devices Is Accurate?
Which Statement Regarding The Usb Standard And Usb Devices Is Accurate? The USB standard and the USB devices will be having four types of wires for communication and for power. Today let us learn about USB ports, USB cables, and USB communication. The USB stands for the universal serial bus, it is aRead more
Which Statement Regarding The Usb Standard And Usb Devices Is Accurate?
The USB standard and the USB devices will be having four types of wires for communication and for power. Today let us learn about USB ports, USB cables, and USB communication. The USB stands for the universal serial bus, it is a standard that is used to connect all the peripherals to the computer. The USB port is the most commonly used port. The name itself represents that the USB port is commonly used in most cases. It can be used in many different ways like scanners, flash drives, cameras, keyboards, and many more. These USB ports can even perform networking and many more. It is also used to charge devices like phones. All the desktops and laptops will be having several USB ports in them.
The main aim of the development of the USB is to connect the devices to the computer. This can be done by first making the standard connector and eliminating all the other connectors. And also by making the connected devices that are easy to configure, and at last by providing the faster transfer rates.
The USB port is hot-swappable which means the devices can be connected or get disconnected without the turning of the computer or the devices. The USB can also self configure itself that can eliminate the requirement of the external configurations.
And by connecting to the computer, the smaller devices can be powered by USB ports without the need for any additional power cables.
The first version of the USB has a transfer speed of 1.5 megabits per second. And the next version has a transfer speed of 12 megabits per second. The USB 2.0 has a high speed with a speed of 480 megabits per second. And in 2008 the USB 3.0 is released that has a super speed of 5 gigabits per second.
The high speed is mainly for transferring large amounts of data, such as the backing up of the external hard drive. The USB 3.1 has a transfer speed of 10 gigabits per second. And the USB 3.2 has a transfer speed of 20 gigabits per second. The USB 4 has a transfer rate of 40 gigabits per second.
We also have different types of cables connectors, ports. The Cables normally have two different connectors on each end cable. They will be having the Type A or Type B or Type C connectors at different ends. The Type A connectors will be the host connector, this is the standard rectangular plug that we would plug into the computers. These computers will be having several type-A USB ports in them.
We can find different types of connectors at the other end of the USN cable like Type B connectors. Type B has a square design, this is the type of connector, that we plug into most of the printers. It can also be used in other devices like external hard drives, microphones, etc. We can also use the mini B connector which is mostly used for smaller devices like smartphones, digital cameras, etc.
See lessWhat Is The Binary Equivalent Of The Decimal Number 232?
What Is The Binary Equivalent Of The Decimal Number 232? 11101000 is the binary equivalent of the decimal number 232. Now, let us discuss how the binary equivalent of the decimal number 232 is found. For suppose if any decimal number is given that to convert into binary, where 232 is the decimal numRead more
What Is The Binary Equivalent Of The Decimal Number 232?
11101000 is the binary equivalent of the decimal number 232. Now, let us discuss how the binary equivalent of the decimal number 232 is found. For suppose if any decimal number is given that to convert into binary, where 232 is the decimal number that we have taken, now we have to find the binary equivalent of the number.
When we are going to convert decimal to any other form, we need to perform the division with the respective number that is taken. The conversion of decimal to decimal is nothing but the power of 2 from the left to right. We can perform this conversion in two methods. The first is the subtraction method and division method. Firstly, let us discuss the subtraction method.
128 64 32 16 8 4 2 1
The above is the sequence of power of 2. Here we do not need to go further to power 2 because the decimal 232 can be found with the above sequence. Now, we are going to add the values that give the sum value equal to the decimal number.
First, fill the number with 1 which has the lowest value after the decimal number 232 in the sequence. Then we get as
128 64 32 16 8 4 2 1
1
Here, after we fill the 128 with 1, the remaining sum which we need to find is 232-128 = 104. And the next lowest number after 104 is 64.
128 64 32 16 8 4 2 1
1 1
After we add 128+ 64 = 192, still we need to add 40 to reach the binary number of 232. So we need to find the next lowest number than 40, that is 32. when we add 32 we get 128+64+32=224
128 64 32 16 8 4 2 1
1 1 1
By subtracting the method, 232-224=8, we know that we need to add 8 more to reach the binary equivalent of the decimal number 232.
128 64 32 16 8 4 2 1
1 1
Now, we got to reach the binary number of 232. Here we have to give the remaining values as 0 which we have not included in the sequence.
128 64 32 16 8 4 2 1
1 1 1 0 1 0 0 0
Hence, the above sequence is the binary equivalent of the decimal number 232.
Now, let us find binary equivalent using the division method. In the division method, we have to divide the number by 2, we get
232 divided by 2 = 232/2 , remainder = 0 and quotient = 116
now, again divide the quotient with 2 116/2, remainder = 0, and quotient=58.
similarly, 58/2, remainder = 0 and quotient = 29
29/2, remainder = 0 and quotient = 14
14/2, remainder = 0 and quotient = 7
7/2, remainder = 1 and quotient = 3
3/2, remainder = 1 and quotient = 1
1/2, remainder = 1 and quotient = 1
Here when take all the remainders from bottom to top, we get the binary equivalent of the decimal number. Then, 1 1 1 0 1 0 0 0.
See lessWhat Routing Metric Affects A Path’s Potential Performance Due To Delay?
What Routing Metric Affects A Path's Potential Performance Due To Delay? The latency will affect a path's potential performance due to delay. Now, let us discuss the routing metrics in detail. We all know that we have several different types of routing protocols. Each of these routing protocols hasRead more
What Routing Metric Affects A Path’s Potential Performance Due To Delay?
The latency will affect a path’s potential performance due to delay. Now, let us discuss the routing metrics in detail. We all know that we have several different types of routing protocols. Each of these routing protocols has unique features and characteristics. These routing protocols can be used for many reasons at some point in the network.
All of these routing protocols will use a metric. Here we will talk about the main purpose of the metric and how it is used. And we also learn about the routing protocol metrics among all other routing protocols.
When multiple updates are received to the same route, in order to determine the best route, we use the routing metrics protocol. The routing can see several updates from all the different routers from the same network. The metric is like a numeric value and the difference between each of the routing protocols can be a small value or can be a large value. The routing protocol can look at the metric of all the similar routes and will use the lowest metric in order to determine the best route. Therefore, we can say that the lower the metric is, the best the route can be.
The routing protocol will look into it, if it didn’t have a metric, it would be having all the updates in the same network. But we wouldn’t know which one will be in the use.
When a router receives several paths to find the destination address, and the one which can make into the routing table is known to be the best path. We can use different methods in order to find the best path.
We assign a value to each path, this is called the metric value. In all of the metric values, we only prefer the lowest metric value. Each router can take the information and will make its own best path to reach the destination.
We have distance-vector routers and link-state routers, they will advertise the network and its metric to the other networks. For suppose, when we cannot find the best route path, then we discard it from the routing table and use the next best path. This is the main advantage of dynamic routing. The routing table can update itself if any changes happened in the network.
There are different metrics that are used by the different routing protocols. The first one is Rip. The rip stands for routing information protocol, this will always use the Hop count as the metric value. Certain types of routing protocols can able to analyze the topology in many ways.
The network service providers can maintain several connections to main the network redundancy. In order to make a better decision and in order to get the exact location, to find the best among the multiple routes., we can use algorithms, rip count can be used to calculate the routing metrics. All these different routing protocols can take different things into consideration.
See lessWhat Utility Is The Equivalent To The Pathping Command On A Linux System?
What Utility Is The Equivalent To The Pathing Command On A Linux System? The system utility is equivalent to the pathing command on a Linux system. Today let us discuss the basic utilities of the Linux system. The utilities are nothing but the basic tools which we use to perform some of the basic taRead more
What Utility Is The Equivalent To The Pathing Command On A Linux System?
The system utility is equivalent to the pathing command on a Linux system. Today let us discuss the basic utilities of the Linux system. The utilities are nothing but the basic tools which we use to perform some of the basic tasks. For example, like the task managers that are into the windows, it is a type of utility that shows all the tasks which are running. We also have disk management, which provides information on how to manage the discs. Here we have many more utilities in the Linux operating system.
Here we can check the processes, we can check the number of tasks which we are going to perform, we can also find the resources, how much the resources get utilized, we can also check their process rates.
For printing of any particular file, we can use the utilities. Pr is the command utility that we give, this command will directly send the information or the file directly to the printer. For sending of the mails, we do not need to install any particular packages, simply by using a tool called mail, we can send the mails.
Now let us check how can we use all those utilities in the Linux terminal. By using the command called the cat, it basically prepares the file into the printable file. The cat command shows the numbers that we added to it. But if this particular page needs to have two different columns while we are printing into the printer. pr -2 name of the file | more. Here the output displays the two columns that have been created on the page.
In the same way, suppose if we want to build three different pages or three different columns, instead of -2 we have to use -3 in it. And if we want to send a mail to any user then we need to define mail -S email name root@localhost and press the enter button. This is the mail that was sent by the trainer user.
After we sent the mail, if we want to check the mail, we need to switch the user to the root, so we should use su root over the command line and we should use the password to the root so that we can check we logged in through the root. After this, we directly need to move into the directory by using the command like # cd/var/spool/mail. Here all user mails are get stored in the var spool mails. Here we can find the different users.
And if we want to check the roots mail, we need to give a command called cat root and then hit the enter button. here we can able to see the mail sent by the trainer, date and its time. These are some of the common utilities that are used. We generally use the PR command that can be used to send the file for printing purposes.
See lessWhich Statement Is True About Cdp On A Cisco Device?
Which Statement Is True About Cdp On A Cisco Device? The main concept in CDP is that it can be able to disable on any specific interface or it can be disabled globally. Today, let us learn about what actually the CDP is and the working of the CDP on a Cisco device. The term CDP stands for cisco discRead more
Which Statement Is True About Cdp On A Cisco Device?
The main concept in CDP is that it can be able to disable on any specific interface or it can be disabled globally. Today, let us learn about what actually the CDP is and the working of the CDP on a Cisco device. The term CDP stands for cisco discovery protocol. The CDP is a protocol that is commonly discussed in Cisco devices. It is like a cisco proprietary protocol that normally works at layer 2 of the OSI model.
Layer 2 of the OSI model is nothing but the data link layer. The main work of this cisco discovery protocol is to learn about all the devices which are directly connected to their physical interface. Or it can be connected across the VLANs. By using this cisco discovery protocol, we can able to know the information about the IP addresses, what is the port is being in use, what is equipment is being in use, and many more. All this information is useful to the people or the users who are new to the network, we can also see where the device uplinks were, where all the switch-up links to the routers.
The cisco discovery process will be the best practice in order to set the whole timer. It is almost three times greater than the cisco discovery packet. The cisco discovery packet is like a frame that we send. It can only take up to 60 seconds to gain all the information in it. When the router can receive the cisco discovery protocol packet, it can able to respond with all the information or details. Now, let us take an example to understand this concept in detail. Let us consider router 1, router 2, and router 3. When all these routers are get connected to each other, the cisco discovery protocol helps to know, which router is connected at what location. If the CDP is not get enabled, we cannot able to see the location of the routers where they are connected or to whom they are connected with.
In order to enable the cisco discovery protocol, we need to use the command called “config t”, this will allows the CDP to be enabled. The cisco discovery protocol can also be dangerous, any user can able to access the network, they can simply connect like a virtual router, which is quite harmful sometimes. If any malicious user is accessed, they will know all the information like Ip details, port information, and also about version numbers. So it can be a bit risky when coming to security if we want to run the cisco discovery router at an open network. So we need to enable the CDP only one some of the specific ports which are risk-free. We need to enable the cisco discovery protocols only on the devices which we have known or on the device where anyone cannot be simply plugged into it. This is a much better thing to do if we want to avoid any malicious users.
See lessWhat Is Indicated By A Successful Ping To The ::1 Ipv6 Address?
What Is Indicated By A Successful Ping To The::1 Ipv6 Address? It is indicated as a TCP/IP stack is correctly get installed in it. Now, let us discuss the::1 IP v6 address in detail. Before we discuss the IPv6 addresses first we need to know why IPv6 has been introducing. When the version of IPv4 waRead more
What Is Indicated By A Successful Ping To The::1 Ipv6 Address?
It is indicated as a TCP/IP stack is correctly get installed in it. Now, let us discuss the::1 IP v6 address in detail. Before we discuss the IPv6 addresses first we need to know why IPv6 has been introducing.
When the version of IPv4 was first introduced, they normally have created nearly billions of IP addresses for all the users. Even though we have a lot of the IP addresses that were created, due to the rapid increase in the usage of electronic devices, the Ipv4 address is run out of stock.
This has lead to the introduction of the IPV6 addresses. Besides the IP version 6 addresses, it brought a lot of improvement when coming to traffic. Now, let us know how actually the IPV6 address looks like?. The Ipv4 is 32 bit in length The structure of the IPv4 contains four sections., which we call the octets, these are get separated by the dots. Each part of the Ipv4 address can contain any number between o to 225.
The IPv6 address is 128 bits long when we compared it with the Ipv4 address. This IPv6 address has a very massive address space than the Ipv4 address. The structure of the IP version 6 has normally eight sections. Each part of this Ipv6 version is called the hextets. The below figure 1.1 represents the structure of the Ip version 6. These eight parts are separated by the colons (:).
The main thing we need to notice in the IPv6 address is that it has letters and numbers in it. The characters of the Ip v6 version can be from 0 to 9 hexadecimal forms. Now, let us know the working of the IP version 6 address in detail.
In Ip v6 version, each of the hexadecimal characters is made up of the four binary bits in it. These bits can be of either 0 or 1. The Ip v6 will double each column from the right to the left. If we see 1 in the IP v6 address, it will toggle the column on, similarly, if we see 0 in the IP v6 address then it will toggle the column off.
Let us understand clearly from figure 1.1 given below, When we see the figure, the first number of the Ip v6 address is 2. Here we may get a doubt how can we represent the number 2 in the binary forms?. Simply, we all know that the binary number of 2 is 0010. Here the number 2 simply stores the binary digit of it. In the same way, it works with the other numbers that follow.
And when we see the characters in the Ip v6 addresses. This character can be from 0 to 9 or it can be from A to F. In the figure, we have the character as D. The D represents 15 when we see it in the hexadecimal form. So here the character D can store the value of up to the 15 numbers in it. This is the way how Ip version 6 works.
See lessWhat Is Contained In The Trailer Of A Data-Link Frame?
What Is Contained In The Trailer Of A Data-Link Frame? The Trailer of a data link frame has all the information about error detection. Today, let us look a closure look into the data link layer. The Data link layer is the second layer of the OSI model. The data link layer is mainly responsible for tRead more
What Is Contained In The Trailer Of A Data-Link Frame?
The Trailer of a data link frame has all the information about error detection. Today, let us look a closure look into the data link layer. The Data link layer is the second layer of the OSI model. The data link layer is mainly responsible for the transferring of the data between the two hosts.
These hosts are directly linked via a network. The data link layer will offer a service called framing. Now, let us learn the concepts of framing in detail. Let us take an example to understand this concept in detail. Let say, we have two devices that are connected through each other. Each has a device, that has an adapter connected to it. This adapter is used to transmit the information between the two devices. Whatever information that we receive from the data link layer, will be converted in the form of signals.
This kind of cable can be transmitted through a medium, which is then received at the physical layer of the OSI model. Now, the main problem here is that the application which has the information will transmit the data in the form of the zeros and the ones. It converts into the transport layer.
In the transport layer, the will add some of the zeroes, ones, and then it transfers to the network layer of the OSI model. After the network layer, it will be gone to the data link layer, in the data link layer, we will add some sets of the zeroes and ones at the header and the trailer part. This addition of zeroes and ones at header and trailer, we call it as the frame.
These frames can only be understood by the data link layer. All the frames will transmit from the host to the host. The framing consists of a header, data, and the trailer part as shown in the below figure 1.1. Here the header part consists of the frame start, its types, quality control and add. And the trailer consists of error detection and the frame stop. And in the middle, we have the exact data which we need to send.
Simply, between the two devices, when they want to communicate with each other knowingly, we use the frame. These frames set a header and trailer at the end of each data in order to get clarity to the receiver where the data gets ended. The header and trailer contain the same information so that the receiver knows the set of information present in a frame.
At the trailer part, we can also find the detection of the errors along with the trailer part. The detection of errors has two techniques, we add some group of bits at the end of the data. So that we can able to detect the errors, another method is the exact count encoding. The below figure shows the format of the data link frame and the sub parts of the data link frame.
1.1
See lessA Network With 10 Bits Remaining For The Host Portion Will Have How Many Usable Host Addresses?
A Network With 10 Bits Remaining For The Host Portion Will Have How Many Usable Host Addresses? A Network with 10 bits remaining for the host portion will have 1022 usable host addresses. Today, let us discuss the network host portions and the host addresses in detail. Normally the IP addresses canRead more
A Network With 10 Bits Remaining For The Host Portion Will Have How Many Usable Host Addresses?
A Network with 10 bits remaining for the host portion will have 1022 usable host addresses. Today, let us discuss the network host portions and the host addresses in detail. Normally the IP addresses can be divided into four portions, each portion consists of a group of eight bits.
All these four portions are again divided into two types. They are network portions and host portions. In each of the classes, there be a network portion and then the host portion. The below figure shows the structure of the network and the host portion.We have seen the network and the host portion, but what exactly do the network portion and the host portion mean?. The main difference between the host and the network device is that the host represents only the single device whereas the network represents the set of all the devices in it. Each and every device that is connected to a network is considered a host. And a set of all these devices that hold is called the network. But why do we use the terms network portion and the host portion differently? We can identify all the hosts, to which network it belongs. Based on the network portion that is given, we can identify whether it belongs to the same network or it belongs to a different network.
Let us take an example to understand this concept in detail. For suppose we have two different Ip addresses 192.168.10.11 and 192.168.10.20, let us assume they are physically connected to each other, since they are physically connected we can call them as in the sam network. But also they logically should be in the same with each other.
When they have the same network portions, then we can call them logically equivalent to each other. When the host has the same network portion, we can say they belong to the same network. Similarly when we observe the two IP addresses. The first three portions are called the network ports and the remaining one is called the host portion. By this, we can say that they are logically in the same network. When they are in the same network portion, then we can say that they can communicate with each other, if all the connectivity is in the proper manner.
These two IP addresses can communicate with each other in an easy manner since they are logically connected together. When the two IP addresses are present in the same class and are in the same network portion, then they are logically equal to each other.
In class A, the first portion must be the same to be logically the same, and in-class B, the first two portions must be the same to be logically together and in class c, all the first three-network portions should be the same in order to be logically together. When there is a slightly different change, then we can say it as they are not on the same network.

See less